- Joined
- Jan 24, 2006
- Location
- South Dakota
So first off I am not sure if this is the correct place to post this.
Currently I have a setup that looks like this:

I am wanting to replace the the firewall with a computer firewall, that computer will host the squid vm and the vm then pushes out to the router etc.

I am trying for a transparent proxy like I currently have set up. I don't want squid exposed to the internet directly which is why I am aiming to have it on a vm instead of as a service on the firewall
So I am wondering what the best way to achieve this is. I was thinking that I should use something like a host-only adapter so that when the internal traffic hits squid, it can push the traffic to its host-only adapter which would then be handled by the firewall and out it goes
However I am having a hard time getting my head around this setup conceptually I dont know if this would work and I don't particularly want to run a double nat unless I have to
Any opinions are welcome!
Currently I have a setup that looks like this:
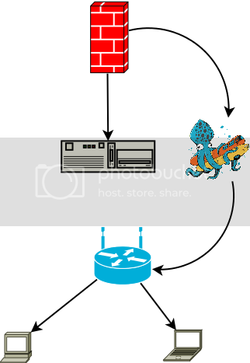
Code:
Internet --> firewall --> server
|__ Squid Vm sitting on server --> wireless router --> internal lan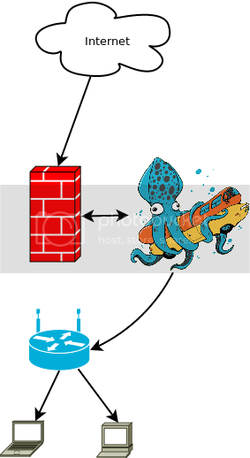
I am trying for a transparent proxy like I currently have set up. I don't want squid exposed to the internet directly which is why I am aiming to have it on a vm instead of as a service on the firewall
So I am wondering what the best way to achieve this is. I was thinking that I should use something like a host-only adapter so that when the internal traffic hits squid, it can push the traffic to its host-only adapter which would then be handled by the firewall and out it goes
However I am having a hard time getting my head around this setup conceptually I dont know if this would work and I don't particularly want to run a double nat unless I have to
Any opinions are welcome!