- Joined
- Jun 14, 2004
I would like some input as, the title states on a security rule... I'm highly simplifying this. In turn, I am willing to give more infrastructure information if need be.
With the Windows Firewall. I am finding out. It is slowing down networked drives access. Mostly after idle and reconnection. Basically, the Windows Firewall is authenticating the machine. Slowing up access times to drives after idle.
(The dedicated drive host machine is my torrent, media, files and general, if it is not on this machine. It is there machine. It is (currently,) an all Windows 7 64bit SP1 Ultimate network. {I'm lazy to install WHS 2011 on the drive host.})
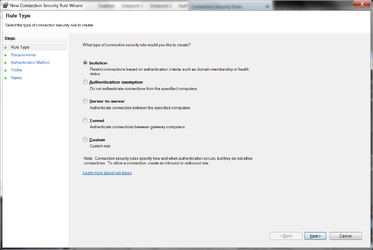
One solution I have to my slow idle access times dilemma. Is to simply have a specific (static) IP connection security exemption rule. I use adapter MAC based static IPs for each machine on the local network. Via my router DHCP. So it is easy to keep specific machines on a static local IP.
i.e. - Machine 192.168.1.2 does not authenticate machines 192.168.1.3-192.168.1.4.
Ok... here is my question... Is there a more elegant and safer way? I know there is a better way. I just haven't come across it or thought of it yet. Any input or suggestions?
With the Windows Firewall. I am finding out. It is slowing down networked drives access. Mostly after idle and reconnection. Basically, the Windows Firewall is authenticating the machine. Slowing up access times to drives after idle.
(The dedicated drive host machine is my torrent, media, files and general, if it is not on this machine. It is there machine. It is (currently,) an all Windows 7 64bit SP1 Ultimate network. {I'm lazy to install WHS 2011 on the drive host.})
One solution I have to my slow idle access times dilemma. Is to simply have a specific (static) IP connection security exemption rule. I use adapter MAC based static IPs for each machine on the local network. Via my router DHCP. So it is easy to keep specific machines on a static local IP.
i.e. - Machine 192.168.1.2 does not authenticate machines 192.168.1.3-192.168.1.4.
Ok... here is my question... Is there a more elegant and safer way? I know there is a better way. I just haven't come across it or thought of it yet. Any input or suggestions?