- Joined
- Dec 1, 2008
- Location
- Last 30 Years NE OH
I'm really considering just to disable UAC, but I'm not sure if it would be the best Idea.I feel pretty safe with current settings, but the real question is about UAC.
I use Comodo Firewall.Its free and very easy to configure.I even have this set up with my vpn.I cant go online without connecting my vpn, and if I lose my vpn, I am automatically cut off.I also have this configured to block out the most commonly hacked ports.When I look in my firewall events, these ports are always getting hit constantly, but there blocked now.( Ports 135-139 )
Some good info below.
***Warning: if running a server on your network these can effect communication with local network peers.
The main reason for using NetBIOS if for two machines to communicate on a local network which rarely is needed except for file and printer sharing on a local network but leaves the door wide open for being hacked. You can remove this risk in two ways and I personally do it both ways.
Firewall: Block ports 135-139 plus 445 in and out. These are used by hackers to steal your info and take control of your pc and after doing so will use NetBIOS to then use your computer to take over another, etc, etc.. Port 137-139 is for Windows Printer and File Sharing but also creates a security risk if unblocked. But if you share a printer on your network you will have to allow this one but I recommend just go to the pc the printer is hooked up to and use. Port 135 is for RPC service on a remote machine. Port 136 is used for Profile Name Service which I don't even think is used any longer but opens a door for hackers.
Disable NetBIOS: Route depends on OS but go to the network connections and find your ethernet adapter which should be called local area connection, right click, click properties, double click TCP/IPv4 in the list, click advanced, click WINS, uncheck LMHosts lookup, choose disable NetBIOS near the bottom. Click ok, ok, ok to close all three windows. Also disable these the same way for the TAP Win32 adapter but LMHost lookup should already be unchecked.
Disable TCP/IP NetBIOS Helper service: From start type services, click services, go down to TCP/IP NetBIOS Helper and right click, click properties, click stop, switch automatically to disabled, click apply, close services.
Remote control ports: You should disable 5500, 5800 and 5900-5903 and 3389 (Windows uses for remote) in and out unless you need remote assistance on your pc which most people do not or do not use this. It's just an open doorway for hackers. This includes software such as VNC. If you ever notice VNC suddenly installed and you didn't then worry a lot and you have already been taken.
Note: If you disable Remote Access Connection Manager it will cause PPTP VPN to not work and connections disappear.
Disable UPnP port 5000: Universal Plug and Play allows your computer to automatically integrate with other network devices. There are known security vulnerabilities associated with this service and should be blocked as well but will eliminate sharing devices on the local network but the risk outways the use. Also it uses port 1900 for UPnP and should be blocked as well. Disable SSDP Discovery service.
You can also disable SMB (server message block) port 445 using regedit. Find HKLM/system/currentcontrolset/services/NetBS/parameters and find transportbindname, delete default value, reboot.
Other ports of interest: 8080 is used for HTTP proxy but also used by hackers to impersonate your pc and hack others. If you don't use a HTTP proxy you might want to block this one. Port 1080 is used for socks proxy and can be attacked and mine is every day by China. Port 500 is for IPSEC VPN use but also listed as a risk to Cisco systems and used mainly to carry the Isass trojan. Other ports known to be directly attacked by a long list of trojans is 21 FTP, 23 telnet dos, 1243, 3128, 3410, 6776, 7000, 12345, 12348, 20034, 27374, 31337. Technically any open port can be a risk but with a good firewall setup correctly you should be stealth for all of these ports. To test commonly attacked ports and check whether you are stealth go here.. https://www.securitymetrics.com/portscan.adp ..also can check here.. http://www.pcflank.com/scanner1.htm ..also.. https://www.grc.com/x/ne.dll?bh0bkyd2
Update: A new customizable port scanner I just found.. http://www.t1shopper.com/tools/port-scan/#
Messenger: Unless you use messenger it's best to uninstall because open up way too many ports and leaves to much at risk. Here are the ports used by MSN Messenger: 135 to get connection port, 1026, 1027, 1028, 1863, 5190, 6891-6900, 6901 voice pc to pc, 2001-2120 voice to phone. Yahoo ports: 80, 5000-5010, 5050, 5100. I'm still working on the different messenger service ports so will update as I go.
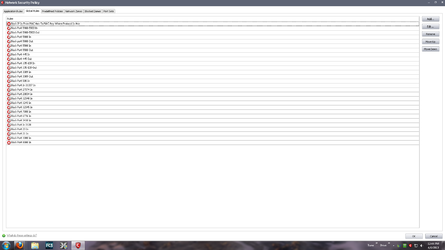
I personal recommend using Comodo Firewall and very easy to use and works perfectly. If using Comodo click firewall tab, advanced, network security policy, global rules click add and setup like illustrated below. It's 2 rules created but just showing the port settings of source and destination of each. To make simpler to understand.. the IN block rule is destination port you choose and source is ANY.. the OUT rule is the port you choose and the destination is ANY.
I use Comodo Firewall.Its free and very easy to configure.I even have this set up with my vpn.I cant go online without connecting my vpn, and if I lose my vpn, I am automatically cut off.I also have this configured to block out the most commonly hacked ports.When I look in my firewall events, these ports are always getting hit constantly, but there blocked now.( Ports 135-139 )
Some good info below.
***Warning: if running a server on your network these can effect communication with local network peers.
The main reason for using NetBIOS if for two machines to communicate on a local network which rarely is needed except for file and printer sharing on a local network but leaves the door wide open for being hacked. You can remove this risk in two ways and I personally do it both ways.
Firewall: Block ports 135-139 plus 445 in and out. These are used by hackers to steal your info and take control of your pc and after doing so will use NetBIOS to then use your computer to take over another, etc, etc.. Port 137-139 is for Windows Printer and File Sharing but also creates a security risk if unblocked. But if you share a printer on your network you will have to allow this one but I recommend just go to the pc the printer is hooked up to and use. Port 135 is for RPC service on a remote machine. Port 136 is used for Profile Name Service which I don't even think is used any longer but opens a door for hackers.
Disable NetBIOS: Route depends on OS but go to the network connections and find your ethernet adapter which should be called local area connection, right click, click properties, double click TCP/IPv4 in the list, click advanced, click WINS, uncheck LMHosts lookup, choose disable NetBIOS near the bottom. Click ok, ok, ok to close all three windows. Also disable these the same way for the TAP Win32 adapter but LMHost lookup should already be unchecked.
Disable TCP/IP NetBIOS Helper service: From start type services, click services, go down to TCP/IP NetBIOS Helper and right click, click properties, click stop, switch automatically to disabled, click apply, close services.
Remote control ports: You should disable 5500, 5800 and 5900-5903 and 3389 (Windows uses for remote) in and out unless you need remote assistance on your pc which most people do not or do not use this. It's just an open doorway for hackers. This includes software such as VNC. If you ever notice VNC suddenly installed and you didn't then worry a lot and you have already been taken.
Note: If you disable Remote Access Connection Manager it will cause PPTP VPN to not work and connections disappear.
Disable UPnP port 5000: Universal Plug and Play allows your computer to automatically integrate with other network devices. There are known security vulnerabilities associated with this service and should be blocked as well but will eliminate sharing devices on the local network but the risk outways the use. Also it uses port 1900 for UPnP and should be blocked as well. Disable SSDP Discovery service.
You can also disable SMB (server message block) port 445 using regedit. Find HKLM/system/currentcontrolset/services/NetBS/parameters and find transportbindname, delete default value, reboot.
Other ports of interest: 8080 is used for HTTP proxy but also used by hackers to impersonate your pc and hack others. If you don't use a HTTP proxy you might want to block this one. Port 1080 is used for socks proxy and can be attacked and mine is every day by China. Port 500 is for IPSEC VPN use but also listed as a risk to Cisco systems and used mainly to carry the Isass trojan. Other ports known to be directly attacked by a long list of trojans is 21 FTP, 23 telnet dos, 1243, 3128, 3410, 6776, 7000, 12345, 12348, 20034, 27374, 31337. Technically any open port can be a risk but with a good firewall setup correctly you should be stealth for all of these ports. To test commonly attacked ports and check whether you are stealth go here.. https://www.securitymetrics.com/portscan.adp ..also can check here.. http://www.pcflank.com/scanner1.htm ..also.. https://www.grc.com/x/ne.dll?bh0bkyd2
Update: A new customizable port scanner I just found.. http://www.t1shopper.com/tools/port-scan/#
Messenger: Unless you use messenger it's best to uninstall because open up way too many ports and leaves to much at risk. Here are the ports used by MSN Messenger: 135 to get connection port, 1026, 1027, 1028, 1863, 5190, 6891-6900, 6901 voice pc to pc, 2001-2120 voice to phone. Yahoo ports: 80, 5000-5010, 5050, 5100. I'm still working on the different messenger service ports so will update as I go.
I personal recommend using Comodo Firewall and very easy to use and works perfectly. If using Comodo click firewall tab, advanced, network security policy, global rules click add and setup like illustrated below. It's 2 rules created but just showing the port settings of source and destination of each. To make simpler to understand.. the IN block rule is destination port you choose and source is ANY.. the OUT rule is the port you choose and the destination is ANY.
Attachments
Last edited: