- Joined
- Jan 24, 2006
- Location
- South Dakota
I have an Ubuntu LDAP server with kerberos setup (I think properly).
Currently the machines I have are
kerberos-server.stratus.local (192.168.122.250, running bind9, Ubuntu 12.04)
client.stratus.local (192.168.122.99, Ubuntu 12.04, authenticates fine against kerberos-server)
centos-rhce.stratus.local (192.168.122.44, CentOS 6.2, Authenticates if logged in as root only)
debian-client.stratus.local (192.168.122.103, Debian Squeeze, authenticates if logged in as root only)
kerberos-server files
/etc/krb5.conf
/etc/krb5kdc/kdc.conf
running ldapsearch from the server
Working Ubuntu Client
/etc/krb5.conf
/etc/pam/d/common-auth
/etc/pam.d/common-session
/etc/nsswitch.conf
Non-working CentOS
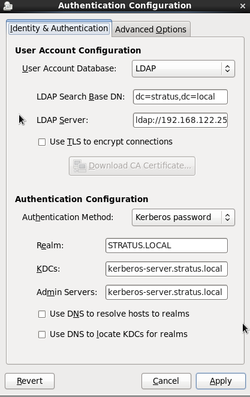
I used the system-config-auth (see the attached screen shot)
The following is in the /var/log/secure (bold indicates that root successfully su'd into john which only exists in ldap)
I have googled around a lot and cant seem to get to the bottom of this. I suspect it has something to do with the fact that when I run an "ldapsearch" I have to specify "-H ldap://kerberos-server.stratus.local" before it will work.
I have the exact same results in debian.
Anyone shed any light on this
EDIT: I should say that both the debian and CentOS machines receive their kerberos tickets just fine (with kinit)
Currently the machines I have are
kerberos-server.stratus.local (192.168.122.250, running bind9, Ubuntu 12.04)
client.stratus.local (192.168.122.99, Ubuntu 12.04, authenticates fine against kerberos-server)
centos-rhce.stratus.local (192.168.122.44, CentOS 6.2, Authenticates if logged in as root only)
debian-client.stratus.local (192.168.122.103, Debian Squeeze, authenticates if logged in as root only)
kerberos-server files
/etc/krb5.conf
Code:
[libdefaults]
default_realm = STRATUS.LOCAL
# The following krb5.conf variables are only for MIT Kerberos.
krb4_config = /etc/krb.conf
krb4_realms = /etc/krb.realms
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
# The following encryption type specification will be used by MIT Kerberos
# if uncommented. In general, the defaults in the MIT Kerberos code are
# correct and overriding these specifications only serves to disable new
# encryption types as they are added, creating interoperability problems.
#
# Thie only time when you might need to uncomment these lines and change
# the enctypes is if you have local software that will break on ticket
# caches containing ticket encryption types it doesn't know about (such as
# old versions of Sun Java).
# default_tgs_enctypes = des3-hmac-sha1
# default_tkt_enctypes = des3-hmac-sha1
# permitted_enctypes = des3-hmac-sha1
# The following libdefaults parameters are only for Heimdal Kerberos.
v4_instance_resolve = false
v4_name_convert = {
host = {
rcmd = host
ftp = ftp
}
plain = {
something = something-else
}
}
fcc-mit-ticketflags = true
[realms]
STRATUS.LOCAL = {
kdc = kerberos-server.stratus.local
admin_server = kerberos-server.stratus.local
}
ATHENA.MIT.EDU = {
kdc = kerberos.mit.edu:88
kdc = kerberos-1.mit.edu:88
kdc = kerberos-2.mit.edu:88
admin_server = kerberos.mit.edu
default_domain = mit.edu
}
MEDIA-LAB.MIT.EDU = {
kdc = kerberos.media.mit.edu
admin_server = kerberos.media.mit.edu
}
ZONE.MIT.EDU = {
kdc = casio.mit.edu
kdc = seiko.mit.edu
admin_server = casio.mit.edu
}
MOOF.MIT.EDU = {
kdc = three-headed-dogcow.mit.edu:88
kdc = three-headed-dogcow-1.mit.edu:88
admin_server = three-headed-dogcow.mit.edu
}
CSAIL.MIT.EDU = {
kdc = kerberos-1.csail.mit.edu
kdc = kerberos-2.csail.mit.edu
admin_server = kerberos.csail.mit.edu
default_domain = csail.mit.edu
krb524_server = krb524.csail.mit.edu
}
IHTFP.ORG = {
kdc = kerberos.ihtfp.org
admin_server = kerberos.ihtfp.org
}
GNU.ORG = {
kdc = kerberos.gnu.org
kdc = kerberos-2.gnu.org
kdc = kerberos-3.gnu.org
admin_server = kerberos.gnu.org
}
1TS.ORG = {
kdc = kerberos.1ts.org
admin_server = kerberos.1ts.org
}
GRATUITOUS.ORG = {
kdc = kerberos.gratuitous.org
admin_server = kerberos.gratuitous.org
}
DOOMCOM.ORG = {
kdc = kerberos.doomcom.org
admin_server = kerberos.doomcom.org
}
ANDREW.CMU.EDU = {
kdc = vice28.fs.andrew.cmu.edu
kdc = vice2.fs.andrew.cmu.edu
kdc = vice11.fs.andrew.cmu.edu
kdc = vice12.fs.andrew.cmu.edu
admin_server = vice28.fs.andrew.cmu.edu
default_domain = andrew.cmu.edu
}
CS.CMU.EDU = {
kdc = kerberos.cs.cmu.edu
kdc = kerberos-2.srv.cs.cmu.edu
admin_server = kerberos.cs.cmu.edu
}
DEMENTIA.ORG = {
kdc = kerberos.dementia.org
kdc = kerberos2.dementia.org
admin_server = kerberos.dementia.org
}
stanford.edu = {
kdc = krb5auth1.stanford.edu
kdc = krb5auth2.stanford.edu
kdc = krb5auth3.stanford.edu
master_kdc = krb5auth1.stanford.edu
admin_server = krb5-admin.stanford.edu
default_domain = stanford.edu
}
[domain_realm]
.mit.edu = ATHENA.MIT.EDU
mit.edu = ATHENA.MIT.EDU
.media.mit.edu = MEDIA-LAB.MIT.EDU
media.mit.edu = MEDIA-LAB.MIT.EDU
.csail.mit.edu = CSAIL.MIT.EDU
csail.mit.edu = CSAIL.MIT.EDU
.whoi.edu = ATHENA.MIT.EDU
whoi.edu = ATHENA.MIT.EDU
.stanford.edu = stanford.edu
.slac.stanford.edu = SLAC.STANFORD.EDU
[login]
krb4_convert = true
krb4_get_tickets = false/etc/krb5kdc/kdc.conf
Code:
[kdcdefaults]
kdc_ports = 750,88
kdc_tcp_ports = 88
default_realm = STRATUS.LOCAL
[realms]
STRATUS.LOCAL = {
database_name = /var/lib/krb5kdc/principal
admin_keytab = FILE:/etc/krb5kdc/kadm5.keytab
acl_file = /etc/krb5kdc/kadm5.acl
key_stash_file = /etc/krb5kdc/stash
kdc_ports = 750,88
max_life = 10h 0m 0s
max_renewable_life = 7d 0h 0m 0s
master_key_type = des3-hmac-sha1
supported_enctypes = aes256-cts:normal arcfour-hmac:normal des3-hmac-sha1:normal des-cbc-crc:normal des:normal des:v4 des:norealm des:onlyrealm des:afs3
default_principal_flags = +preauth
}
[logging]
kdc = FILE:/var/log/kdc.logrunning ldapsearch from the server
Code:
root@kerberos-server:/etc/krb5kdc# ldapsearch -x -b dc=stratus,dc=local
# extended LDIF
#
# LDAPv3
# base <dc=stratus,dc=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# stratus.local
dn: dc=stratus,dc=local
objectClass: top
objectClass: dcObject
objectClass: organization
o: stratus
dc: stratus
# admin, stratus.local
dn: cn=admin,dc=stratus,dc=local
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
# people, stratus.local
dn: ou=people,dc=stratus,dc=local
objectClass: organizationalUnit
ou: people
# groups, stratus.local
dn: ou=groups,dc=stratus,dc=local
objectClass: organizationalUnit
ou: groups
# john, people, stratus.local
dn: uid=john,ou=people,dc=stratus,dc=local
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
uid: john
sn: Doe
givenName: John
cn: John Doe
displayName: John Doe
uidNumber: 1000
gidNumber: 10000
gecos: John Doe
loginShell: /bin/bash
homeDirectory: /home/john
shadowExpire: -1
shadowFlag: 0
shadowWarning: 7
shadowMin: 8
shadowMax: 999999
mail: [email protected]
postalCode: 31000
l: Toulouse
o: Stratus
mobile: +33 (0)6 xx xx xx xx
homePhone: +33 (0)5 xx xx xx xx
title: System Administrator
postalAddress:
initials: JD
# example, groups, stratus.local
dn: cn=example,ou=groups,dc=stratus,dc=local
objectClass: posixGroup
cn: example
gidNumber: 10000
# search result
search: 2
result: 0 Success
# numResponses: 7
# numEntries: 6
root@kerberos-server:/etc/krb5kdc#Working Ubuntu Client
/etc/krb5.conf
Code:
[libdefaults]
default_realm = STRATUS.LOCAL
# The following krb5.conf variables are only for MIT Kerberos.
krb4_config = /etc/krb.conf
krb4_realms = /etc/krb.realms
kdc_timesync = 1
ccache_type = 4
forwardable = true
proxiable = true
kdc = 192.168.122.250
# The following encryption type specification will be used by MIT Kerberos
# if uncommented. In general, the defaults in the MIT Kerberos code are
# correct and overriding these specifications only serves to disable new
# encryption types as they are added, creating interoperability problems.
#
# Thie only time when you might need to uncomment these lines and change
# the enctypes is if you have local software that will break on ticket
# caches containing ticket encryption types it doesn't know about (such as
# old versions of Sun Java).
# default_tgs_enctypes = des3-hmac-sha1
# default_tkt_enctypes = des3-hmac-sha1
# permitted_enctypes = des3-hmac-sha1
# The following libdefaults parameters are only for Heimdal Kerberos.
v4_instance_resolve = false
v4_name_convert = {
host = {
rcmd = host
ftp = ftp
}
plain = {
something = something-else
}
}
fcc-mit-ticketflags = true
[realms]
STRATUS.LOCAL = {
kdc = kerberos-server.stratus.local
admin_server = kerberos-server.stratus.local
}
[domain_realm]
.stratus.local = STRATUS.LOCAL
stratus.local = STRATUS.LOCAL
testing@client:/etc/pam.d$/etc/pam/d/common-auth
Code:
testing@client:/etc/pam.d$ cat common-auth |grep -v "#"
auth [success=2 default=ignore] pam_unix.so nullok_secure
auth [success=1 default=ignore] pam_ldap.so use_first_pass
auth requisite pam_deny.so
auth required pam_permit.so
auth optional pam_cap.so/etc/pam.d/common-session
Code:
testing@client:/etc/pam.d$ cat common-session |grep -v "#"
session [default=1] pam_permit.so
session requisite pam_deny.so
session required pam_permit.so
session optional pam_umask.so
session required pam_unix.so
session optional pam_ldap.so
session optional pam_ck_connector.so nox11
session required pam_unix.so
session required pam_mkhomedir.so skel=/etc/skel/
session optional pam_ldap.so
session optional pam_foreground.so/etc/nsswitch.conf
Code:
testing@client:/etc/pam.d$ cat /etc/nsswitch.conf |grep -v "#"
passwd: compat ldap
group: compat ldap
shadow: compat ldap
hosts: files mdns4_minimal [NOTFOUND=return] dns mdns4
networks: files
protocols: db files
services: db files
ethers: db files
rpc: db files
netgroup: nisNon-working CentOS
I used the system-config-auth (see the attached screen shot)
The following is in the /var/log/secure (bold indicates that root successfully su'd into john which only exists in ldap)
Code:
[b]May 4 09:50:43 389-second su: pam_unix(su:session): session opened for user john by stratus(uid=0)
May 4 09:50:45 389-second su: pam_unix(su:session): session closed for user john
May 4 09:50:46 389-second su: pam_unix(su:session): session closed for user root[/b]
May 4 09:50:50 389-second unix_chkpwd[3148]: password check failed for user (john)
May 4 09:50:50 389-second su: pam_unix(su:auth): authentication failure; logname=stratus uid=500 euid=0 tty=pts/1 ruser=stratus rhost= user=john
May 4 09:50:50 389-second su: pam_krb5[3144]: authentication fails for 'john' ([email protected]): User not known to the underlying authentication module (Client not found in Kerberos database)I have googled around a lot and cant seem to get to the bottom of this. I suspect it has something to do with the fact that when I run an "ldapsearch" I have to specify "-H ldap://kerberos-server.stratus.local" before it will work.
I have the exact same results in debian.
Anyone shed any light on this
EDIT: I should say that both the debian and CentOS machines receive their kerberos tickets just fine (with kinit)
Attachments
Last edited: